The 5-Second Trick For Risk Management Enterprise
Table of Contents3 Easy Facts About Risk Management Enterprise DescribedSome Ideas on Risk Management Enterprise You Should KnowThe Ultimate Guide To Risk Management Enterprise
Control who can check out or modify these elements by establishing certain accessibility rights for specific customers, making certain info safety and tailored functionality. Enables individuals to customize their interface by choosing and setting up essential data components. Supplies an individualized experience by allowing modification of where and how data elements are presented.It allows accessibility to real-time incorporated information immediately. Facilities can use extensive information intelligence for quicker and more educated decision-making.
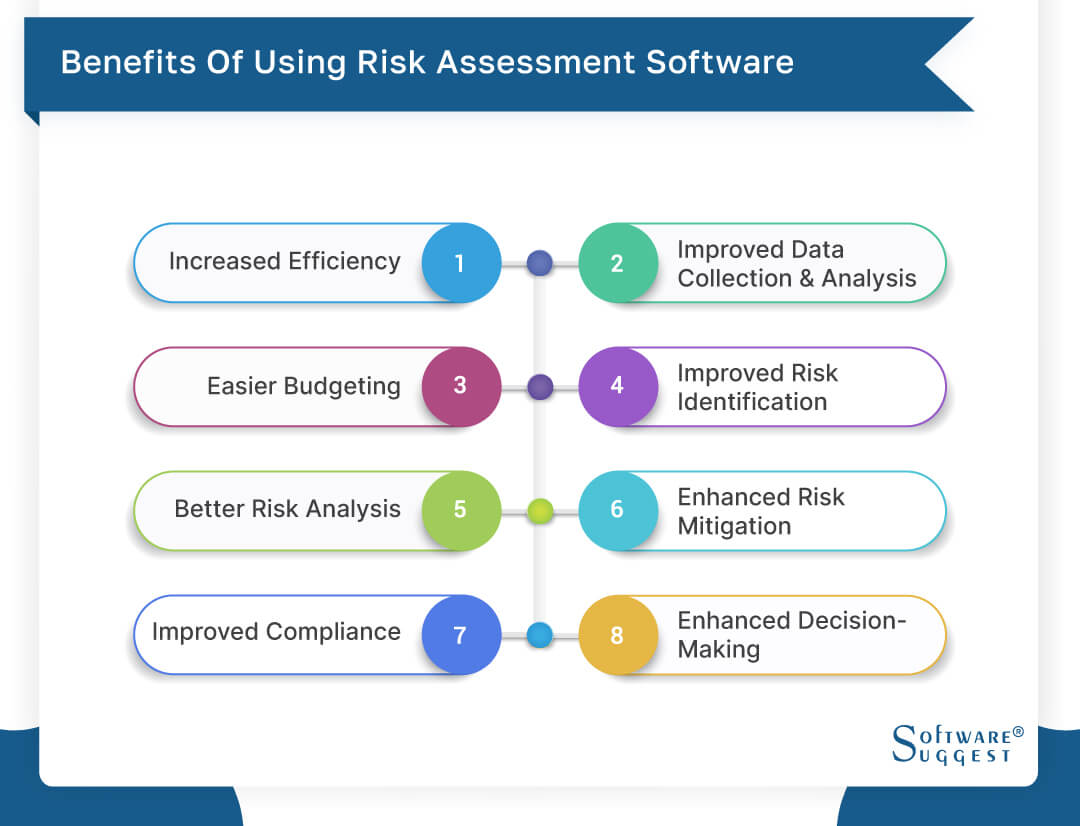
Diligent is a danger monitoring software program that allows enhancing efficiency, and increases growth. It likewise helps monitor risks with ERM software that consists of incorporated analytics and adapts to your company requirements.
The 8-Second Trick For Risk Management Enterprise
Streamlines the procedure of collecting danger information from various parts of the organization. Supplies management and the board with real-time threat insights. Use ACL's advanced analytics to find threat patterns and forecast dangers.
This allows business to catch threat understandings and warnings in the third-party vendor's security report. This enables conserving threat assessments as auditable documents. It also permits exporting them as PDFs. To finish look at more info the procedure firms can complete a review day. Allows business to record and record danger understandings and red flags in third-party vendor safety records.
It additionally lowers danger via structured compliance and danger monitoring. It can assist gather and track all your threats in the Hyperproof risk register.
It gives quick access to essential details and paperwork. This ensures the safety and security of Active proof instances by making it possible for multi-factor authentication (MFA) using authenticator apps such as Google Authenticator, Microsoft Authenticator, or Authy.
Risk Management Enterprise for Dummies
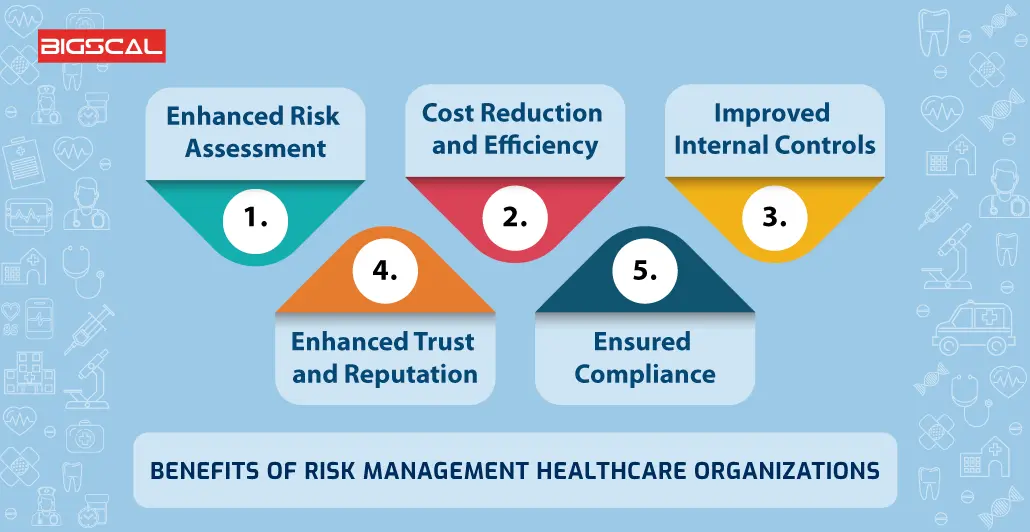
It supplies top-tier useful link safety and security attributes to guard sensitive data. This threat administration software application is an excellent device for centers looking to repair unneeded problems or threats.
Users moved here can additionally make use of the AI-powered tools and pre-existing material to produce, examine, prioritize, and address threats successfully. Streamlines the process of configuring and populating risk registers. Utilizes AI and library material to improve danger analysis accuracy. It enables quicker recognition and mitigation of risks, This is generally a visual model.